A horrifying report by The Verge details the unsavoury evidence of password managers being exploited in order to serve targeted ads. The method had first been described and detected by Princeton’s Center for Information Technology Policy, which we had already featured in one of our articles on tracking.
The method exploits both the in-built browser password managers and third-party plug-ins such as LastPass. These password managers usually automatically fill out the password forms for you when they recognise them.
The Method
When your browser automatically fills out a password form, the data it fills it with can be used to track you. The principle is simple – the website presents you with a genuine login form that you use to login. Then, the same form is present on all the other pages on that or other websites, but in a hidden form. Your browser still fills it out and the script sends a hashed from of that e-mail to third-party servers.
Some of the scripts also collect other information as well, including browser, OS and localisation information as well as CPU type. The researchers examined two scripts – AdThink and OnAudience, but they are a drop in the ocean.
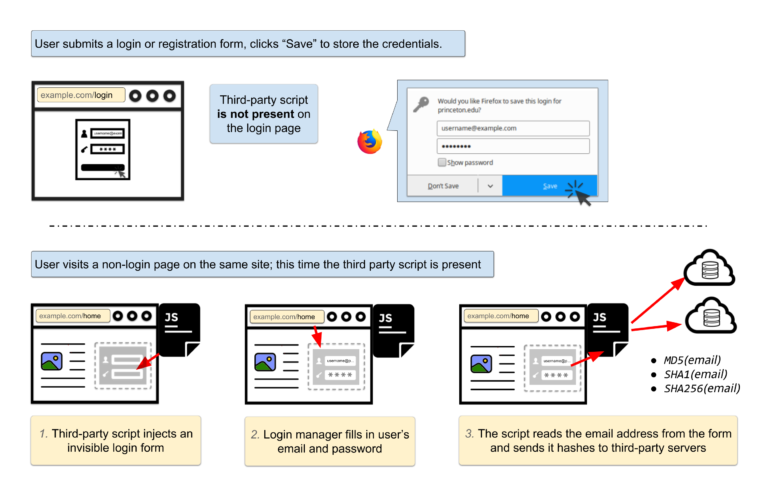
A flowchart of the attack. © Princeton Center for Information Technology Policy
Guess what is then done with your data? You’re right, it’s being sold – your cross-site advertising ID is available to the highest bidder and there’s very little you can do about it. According to The Verge, AdThink claimed the script was only experimental and accounted for a small percentage of total data collected.
Countermeasures
Luckily, these scripts don’t steal passwords or e-mails as it is. Such password theft is extremely rare (though possible), and these scripts are generally capable of collecting passwords with just a few simple tweaks.
This vulnerability is nothing new. Cross-site scripting and auto-fill features simply don’t go hand in hand, and researchers have been warning against it for over a decade.
You can help prevent potential security issues by using a different password for each of the websites you visit. That way at least you won’t risk compromising all your accounts if a rogue script takes over. The nuclear option such as the NoScript plugin is also becoming more and more reasonable. Vanilla ad-blockers will likely add these scripts to their blocklists as well.
Consider disabling autofill options in your browser, such as the ‘signon.autofillForms’ preference in Firefox.
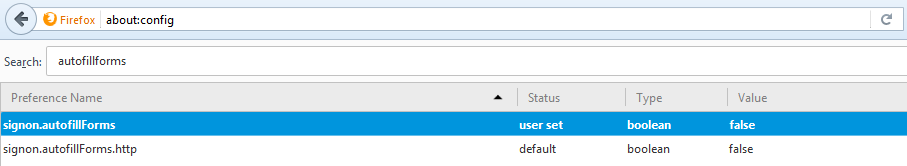
The preference is buried in the about:config feature.
In the future, new W3C guidelines stipulate mandatory notification whenever a browser provides credential to a page, which will allow users to more easily detect this sneaky practice. You can also try to opt out of AdThink tracking script here.
Password managers that do not auto-fill your passwords (1Password and Keeper come to mind) are not vulnerable to this attack.
Is It Legal?
The Venn diagram of websites that use these scripts and care about their legality is just about empty. Thus, this is largely an academic question in the Wild West that is the Internet. In the European union, at least when the GDPR rolls out, things are looking grim for this method of data collection.
Even if today this practice were shown to be legal, the sheer act of burying these terms under obscure privacy and usage policies is forbidden under the GDPR. Thus, without explicit consent and notification such data collection will be patently illegal under the GDPR. As for fining the offending companies, we are much less optimistic in this regard, sadly.
Conclusion
This is a cause for concern. The researchers found the script on only 1100 out of top 1 million Alexa sites, but the adoption of these scripts can spread like wildfire. It’s a major problem that essentially clandestinely steals very confidential data from regular users and presents a huge breach of trust between website owners and users. This time, the advertising camp really took it too far.
Update 7 Feb 2018: We received an official statement from Cloud Technologies (OnAudience.com). You can read it in full here.







